Improved Biba model based on trusted computing - Liu - 2015 - Security and Communication Networks - Wiley Online Library

Two Laws of Biba Model The satisfaction of both Biba laws, prevents the... | Download Scientific Diagram
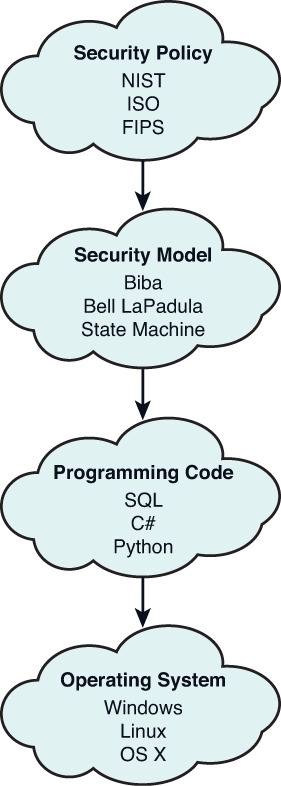
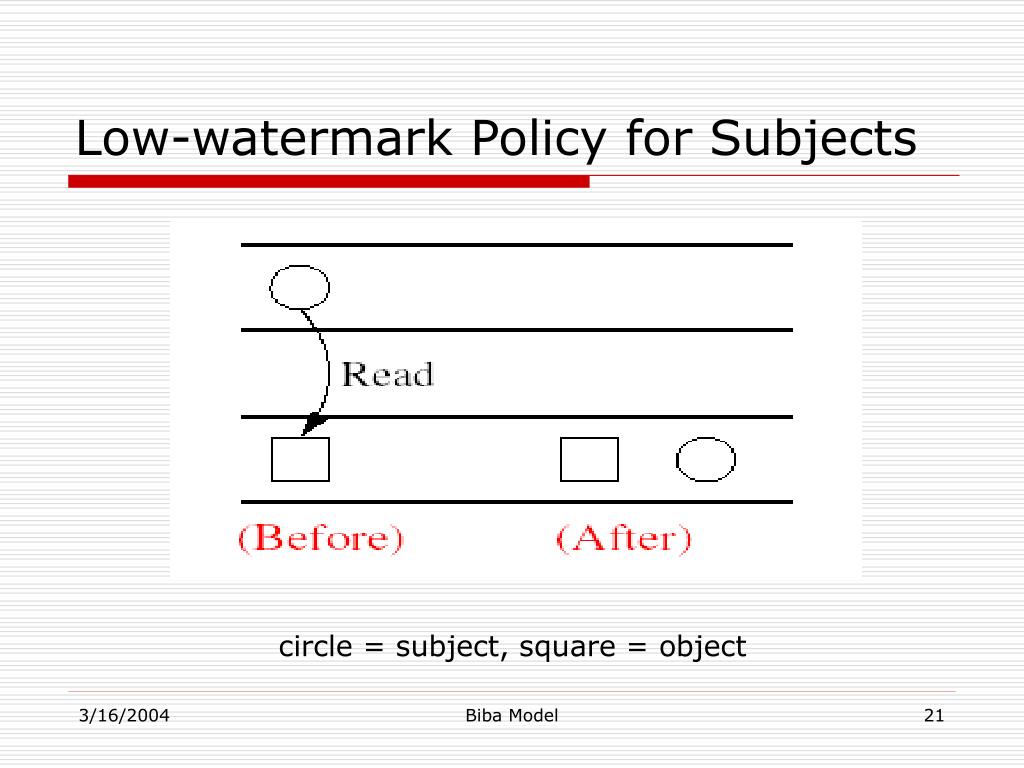
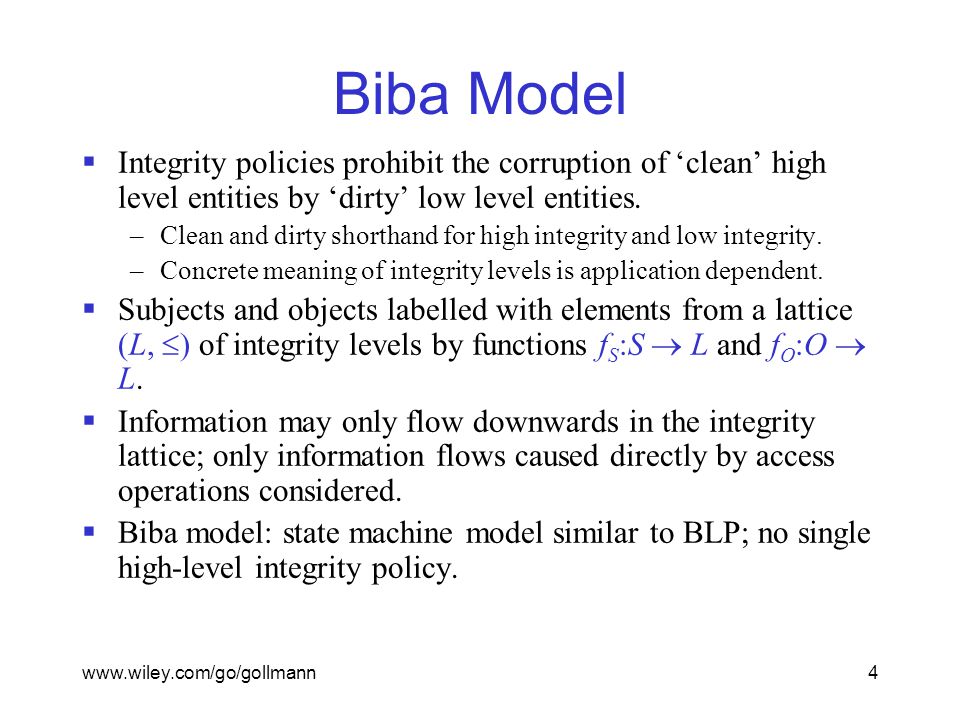
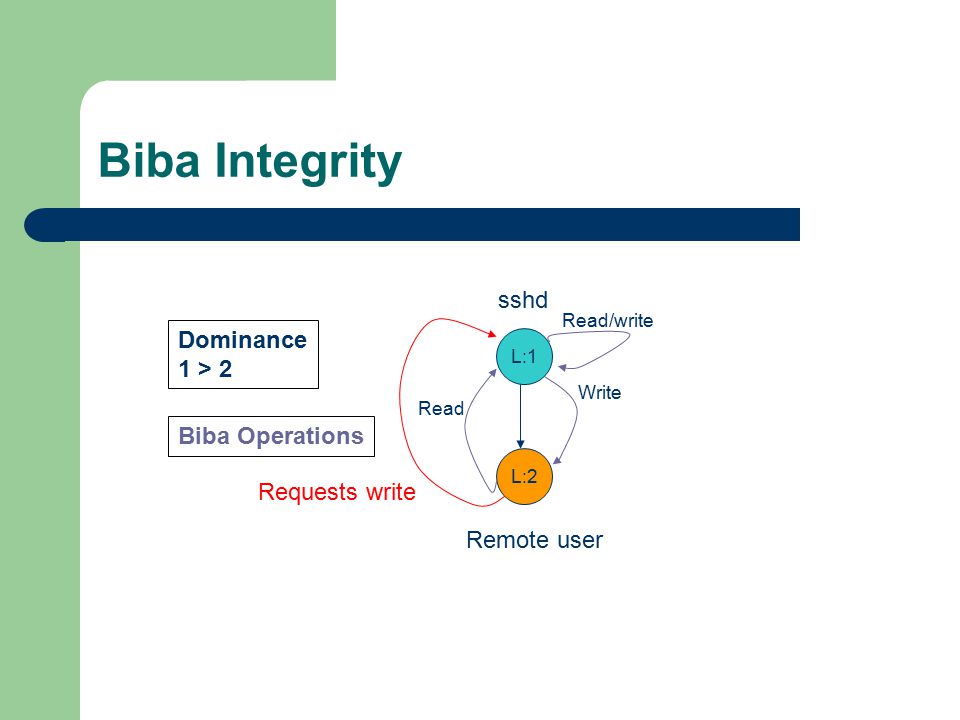
Integrity Models Biba Integrity Model (1977) Biba Model – ”no read down” Biba Model – ”no write up” Biba Model – i

Two Laws of Biba Model The satisfaction of both Biba laws, prevents the... | Download Scientific Diagram
A NEW MLS MANDATORY POLICY COMBINING SECRECY AND INTEGRITY IMPLEMENTED IN HIGHLY CLASSIFIED SECURE LEVEL OS